Server Dashboard
Activity
Live Query Statistics
Profiler
Server Memory
Waits
Error Log
Cpu
IO
SQL Queries
Healthcheck
Databases
Database
Tables/Partitions
Index Use
Index Fragmentation
Files
Locks
Memory
SQL Queries
Default Trace
Transaction Log
Healthcheck
Execution Plan View
Index Maintenance
Manual Index Analysis
Index Defragmentation Jobs
Alerts
Configuration
Slack Integration
Teams Integration
Custom SQL Alerts
Maintenance Windows
SQL Server Alerts List
Activity
Live Query Statistics
Profiler
Server Memory
Waits
Error Log
Cpu
IO
SQL Queries
Healthcheck
Databases
Database
Tables/Partitions
Index Use
Index Fragmentation
Files
Locks
Memory
SQL Queries
Default Trace
Transaction Log
Healthcheck
Execution Plan View
Index Maintenance
Manual Index Analysis
Index Defragmentation Jobs
Alerts
Configuration
Slack Integration
Teams Integration
Custom SQL Alerts
Maintenance Windows
SQL Server Alerts List
Once installed the service logon account should be set to something other than "Local System Account". Although this account will normally allow the service to run it is more convenient to use a network account that has sufficient permissions on the SQL Servers that will be monitored, so Windows credentials can be used to connect to all SQL Servers.
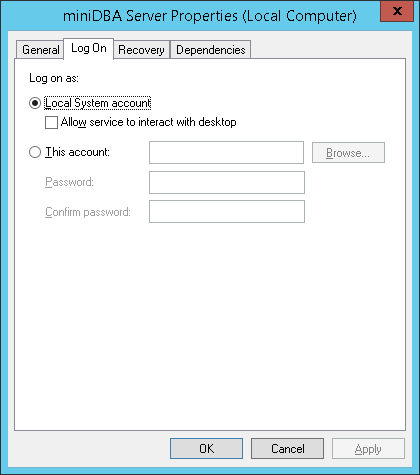
The above screenshot shows the logon being set to "Local System Account" which normally has enough permissions locally to access all the resources it needs to.
It is recommended that you use an existing or create a new network account that has permissions to access files on the local server and also the correct permissions on the SQL Servers that will be accessed.
The Windows account needs FULL CONTROL permission on the 'C:\ProgramData\miniDBA' Server folder.
The VIEW SERVER STATE permission is the minimum that the network account should be granted on each SQL Server to allow miniDBA to monitor it.
Databases will only be visible to miniDBA if the login being used by miniDBA has VIEW DATABASE STATE permission for each database.
miniDBA cannot tell you this information if it does not have VIEW DATABASE STATE so run this query to see which databases the current login has the permission for:
See the trouble shooting page if you have any issues or go to getting started for your next steps.

The above screenshot shows the logon being set to "Local System Account" which normally has enough permissions locally to access all the resources it needs to.
It is recommended that you use an existing or create a new network account that has permissions to access files on the local server and also the correct permissions on the SQL Servers that will be accessed.
The Windows account needs FULL CONTROL permission on the 'C:\ProgramData\miniDBA' Server folder.
The VIEW SERVER STATE permission is the minimum that the network account should be granted on each SQL Server to allow miniDBA to monitor it.
Databases will only be visible to miniDBA if the login being used by miniDBA has VIEW DATABASE STATE permission for each database.
miniDBA cannot tell you this information if it does not have VIEW DATABASE STATE so run this query to see which databases the current login has the permission for:
DECLARE @sql varchar(2000)
DECLARE @db varchar(200)
DECLARE @dbs3 table(name varchar(200))
CREATE TABLE [#perms_{1}] (db varchar(200), [perm] varchar(100))
INSERT @dbs3 (name) select name from sys.sysdatabases WHERE ISNULL(HAS_DBACCESS ([Name]),0)=1
SET @db = (select top(1) name from @dbs3 )
print @db
WHILE @db is not null
BEGIN
set @sql = 'use [' + @db + ']
INSERT [#perms_{1}] SELECT db_name(), permission_name FROM fn_my_permissions(NULL, ''DATABASE'')'
exec(@sql)
delete top (1) from @dbs3
set @db = (select top(1) name from @dbs3)
END
SELECT * FROM [#perms_{1}]
WHERE perm = 'VIEW DATABASE STATE'
DROP TABLE [#perms_{1}]
See the trouble shooting page if you have any issues or go to getting started for your next steps.